Importing the Root CA
After the PAP tests have passed, the EAP tests have passed with the "snake oil" certificates, and the production certificates have been created and tested, the CA certificate needs to be added to each client machine that performs EAP authentication.
The simplest way to do this is to copy the file ca.der file from the /etc/raddb/certs directory to Windows desktop, and then double-click on it. This should start the process of importing the certificate into the Windows certificate store.
If double-clicking on the file does not work, see the EAP-TLS Howto on the main FreeRADIUS site for more detailed instructions, with screenshots. That document calls the CA certificate root.der rather than ca.der, but it has the same meaning.
Once the ca.der file is imported onto the client system, ensure that the Validate Server Certificate option is checked in the 802.1X supplicant (e.g. Windows laptop). Other supplicants (e.g. Mac OSX, or wpa_supplicant) use different methods for configuring a known certificate. See their documentation for more information.
For command line testing, see eapol_test.
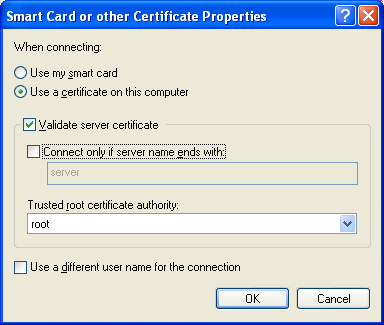
Then, login using the user name and password from the PAP howto. (Which we assume you have already followed.) If all goes well, the server should send back an Access-Accept packet.
When the above method is used, the following authentication types should just work:
- PEAPv0
- EAP-GTC
- EAP-MSCHAPv2
- EAP-TTLS
- PAP
- CHAP
- MS-CHAP
- EAP-MD5
- EAP-MSCHAPv2
At this point, there are only a few things that can go wrong. See the EAP problems page for some common problems and solutions.
If everything works, then congratulations, you have successfully configured the hardest parts of EAP authentication.
